Ignite
Ignite is a simple challenge to practice your pentesting skills.
Recon
As always we start with nmap
sudo nmap -sC -sV -oA nmap/ignite $IPAnd we get the following output
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))Only one port is open, Apache httpd 2.4.18.
Upon opening the webpage we are greeted with Welcome to Fuel CMS version 1.4.
This directly tells us what to search for vulnerabilities.
Looking through the page, this seems the default page when you first setup Fuel CMS.
At the end of the page it tells you where the admin login is with the default credentials.
Once logged lets search online for some exploits and we can see that there is a Remote Code Execution exactly for version 1.4.
Remote Code Execution
I'll be using the payload from this exlploit, however I'll exploit it using BurpSuite to manually use the exploit.
Reading the python script, we can see that it basically sends a payload to /fuel/pages/select/?filter variable which can execute system commands.
Lets navigate to the pages page on the left and start up BurpSuite. (If you don't know how to use Burp, I would highly recommend to checkout some tutorials online or if you're subscribed to THM check out this room).
Once you have your proxy and Burp setup, simply refresh the page to capture the request.
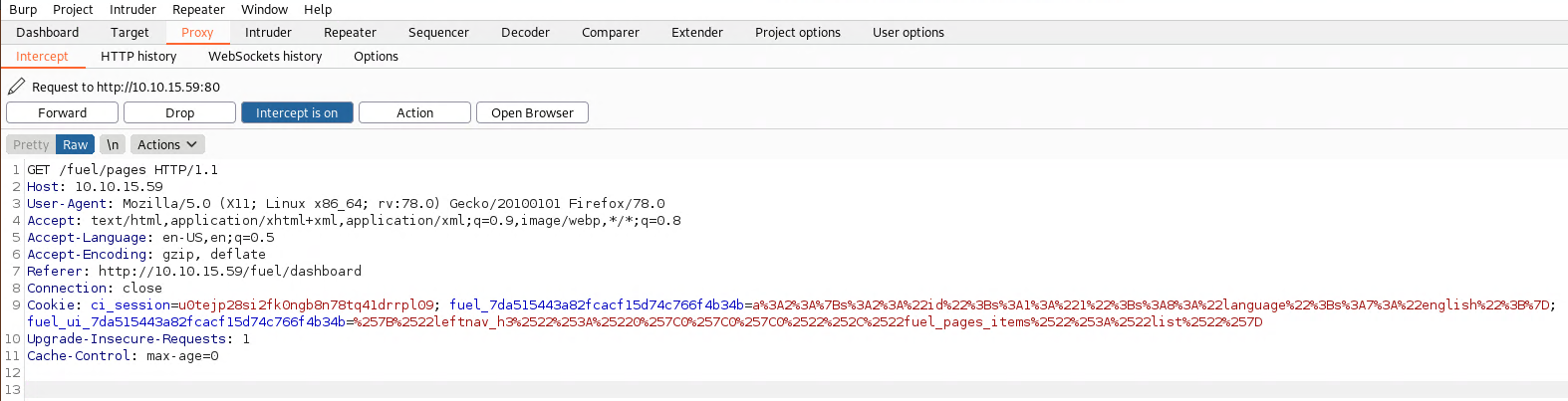
And send this to Repeater (Ctrl + R)
Now lets grab the payload and modify it by removing the urlib.quote variable (with the +) and simply put ls.
and paste it next to the URL and press send.

And in the response you should see files in the current directory.
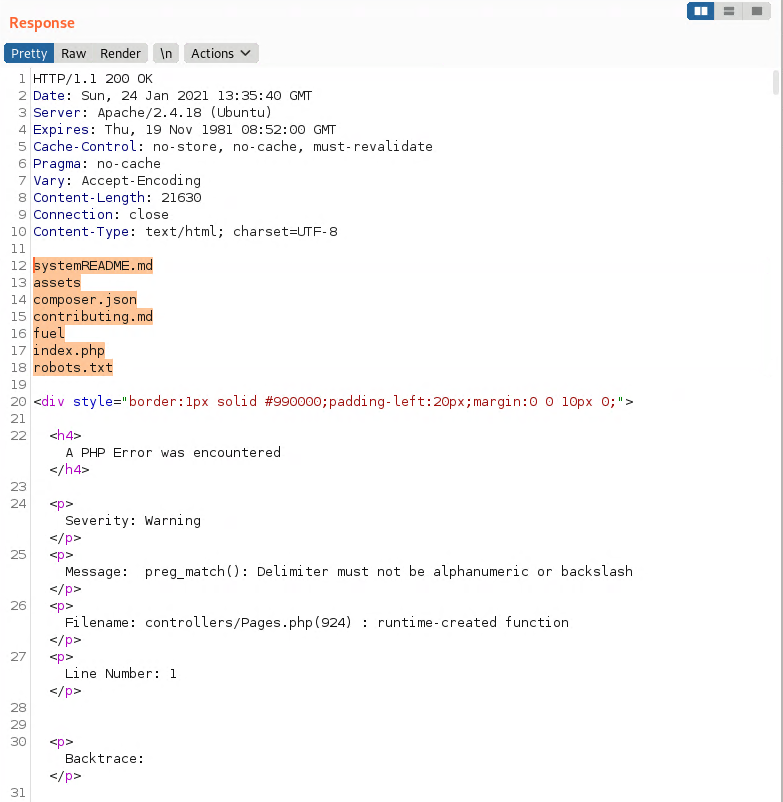
Awesome! We can execute commands on the system.
Now lets get a reverse shell.
I've tried a few reverse shells and the one that works for me is NetCat OpenBSD (Here is a cheatsheet).
Lets copy our URL encoded payload and send it to Decoder and decoded it as URL.
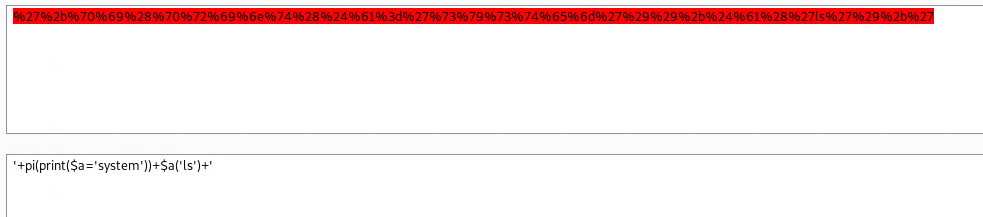
Paste your reverse shell command instead of ls(with the single quotes).
And encode it as URL.
Start up ncat on your local machine to listen on your desired port.
Copy the URL Encoded payload and replace it with the current one you have in Repeater and Send it.
You shouldn't receive any response.

And it stead you should get a shell back.
Privesc
Once you're in, always and I say always stabilize your shell!.
This applies to Linux machines.
Do the following steps.
Python will spawn you in a bash shell, setting the TERM to xterm will allow you to use clear and stty will let you use Ctrl + C, arrow keys and TAB completion.
The user flag is in the /home directory.
Now it's time to escalate our privileges. To save you the trouble, I tried using LinEnum, linPeas, exploit suggester to see if I can find anyway to exploit this box but there was nothing I can find.
If www-data has a home directory, then maybe we can run sudo -l, however that didn't help.
So that means that there are some credentials stored in a file. I started to snoop around the Fuel CSM GitHubrepo and found an interesting file.
There is a database.php file where it keeps user credentials. GitHub repo.
Reading the file we discover the credentials for root.

With this you get root on the box and the root flag is in /root.
Conclusion
Ignite was quite an easy box. I decided to do a manual exploit with Burp since it makes you use your brain to think of ways to exploit something. Using already made scripts to exploit the box will not teach you anything.
I get these inspirations from IppSec Link to his YouTube channel. He does video tutorials on how to exploit machines on HackTheBox which are very well made and explained.
That is how I got the idea to search the GitHub repo for Fuel CMS to search if there are any default files that might store some valuable information.
I'd suggest you do research on the things you'll be attacking. You never know if you can find something really important online.
Last updated